Multi-factor authentication (MFA)
This page includes: Setting up MFA, What will MFA look like on a day-to-day basis and Frequently Asked Questions.
What is Multi-Factor Authentication?
Multi-Factor Authentication (MFA) provides an additional layer of protection for software systems and the data they contain. In practice this means you will need to perform one extra step to log in to any HESA system that you use. This change is driven by HESA’s commitment and obligation to maintain the highest standards of information security and data protection. Implementation of MFA has been specifically recommended by the Information Commissioner’s Office and is essential to ensure the security of the personal data processed in HESA systems.
Access to HESA systems is controlled by the HESA Identity System (IDS). When you log in to any of the systems below you currently use an IDS username and password. From 21 April 2022 after you enter your password you will be asked to authenticate your log-in via a third-party app on your phone.
The HESA systems controlled by IDS log-on are:
- Identity System
- HESA Data Collection System
- HESA Data Platform
- Issue Management System
- Graduate Outcomes Portal
- Heidi Plus
Authenticator Apps
Our Time-based One Time Passwords are generated in line with industry standards, meaning that any mainstream authenticator app should be compatible. Some password managers have also added support for this functionality too. Please contact your IT or Information Security department to discuss your requirements.
Examples of authenticator applications which we have tested are listed in the FAQ Which third party authenticator apps can I use? below. Please note that HESA does not endorse any particular third-party application for this purpose.
Setting up MFA
From 21 April 2022, you will be required to set up MFA with your IDS account via an authenticator app. These are the steps involved in setting up MFA.
Login to the Identity System as normal, you will be prompted to re-accept the IDS General Terms and Conditions.
Once the Terms and Conditions have been accepted, a QR code should then appear (see screenshot below). You will need to scan this with your smart phone on your chosen authenticator app linking your phone to your IDS account. This will present you with a 6 digit verification code. An alternative method could be to enter the 'User Secret' code manually on your authenticator app, again linking your phone to your IDS account.
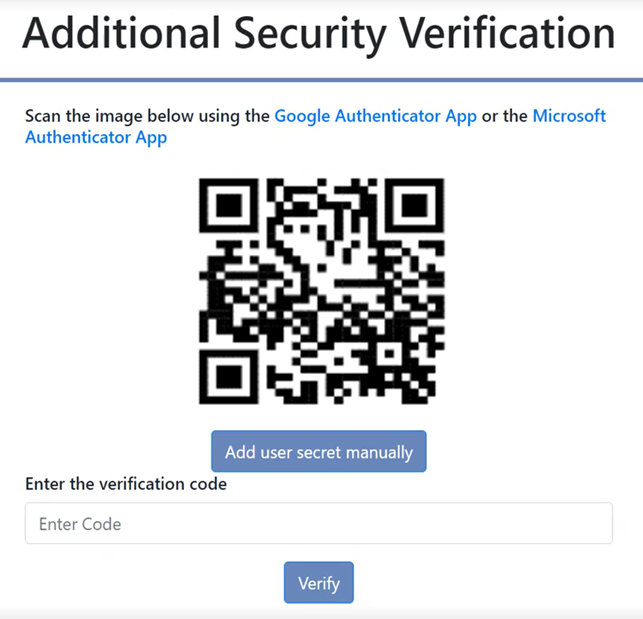
After the correct code has been entered, you will be directed to a page which contains your 6 unique recovery codes. These codes should be downloaded and saved on your computer. More information on Recovery Codes please see below. Once you have saved your 6 recovery codes and clicked continue you will be re-directed back to the initial sign in page and a message/banner should appear now letting you know you have setup MFA.
Logging into IDS once MFA is set up
Signing into Identity System will direct you to a standard verification page (see screenshot below). To access your verification code you will need to log into your authenticator app. As MFA has been set up, the IDS account should be saved on your authenticator app and will be ready with a new 6 digit code.
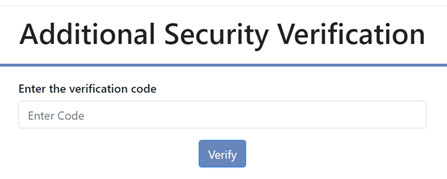
Finally, once the correct 6 digit verification code has been entered, you will be granted access to IDS, and/or any other desired system that is governed by IDS.
What are Recovery Codes?
Recovery codes are used to transfer a user’s existing MFA setup. This should be used in instances where a user would like to transfer their existing MFA setup to a new device. They will always be present from when a user signs up for MFA. They appear once the QR code is scanned and the correct code has been entered. You will then need to save them as they will not appear again.
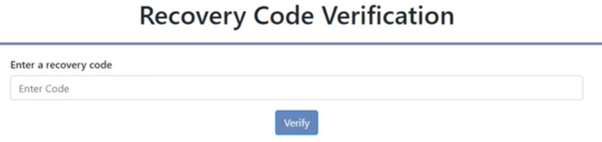
When would a user be prompted to input a recovery code? Users can select ‘Use a recovery code’ following an attempt to log in to the HESA Identity System using their email address and password. Selecting the ‘Use a recovery code’ link will direct the user to a new webpage where a recovery code can then be entered.
How many codes are created? There will be 6 one-time recovery codes generated upon setting up MFA, all with ability to recover MFA on a new device.
If a user still uses their phone but has either forgotten it or temporarily lost it, can they still use their recovery codes? Yes
When and where should recovery codes be used? The recovery codes are generated during the setup of MFA once the QR code has been scanned and the verification code has been entered. Your codes are provided as a text file download.
How many times are the codes viewable? Codes are viewed only once at the point of setting up MFA. We suggest downloading and saving your 6 unique codes as they are not viewable again.
Scenario: A user of IDS has upgraded their phone.
Logging in
A user has upgraded their phone and would like to transfer their MFA setup to their new phone. When setting up their initial MFA the user would have saved their 6 recovery codes onto their computer. When logging in, they should use one of their recovery codes. This is done by clicking the link below the box a user would usually enter their 6 digit verification code into. Once they have then entered their recovery code into the required box, they will be redirected to the main IDS user page.
Transferring MFA,
On the main IDS page you will need to select ‘My Account’ and ‘MFA setup. A new QR code will be displayed and the user will be prompted to follow the initial MFA set up steps. Please see Setting up MFA for further guidance.
What will MFA look like on a day-to-day basis?
Once MFA has been set up against your Identity System, you will be able to access any HESA system you have been granted access to. When logging into your desired system, you will be asked to enter / confirm you email and password. Once entered correctly, you will need to open your authenticator app and enter the 6 digit code that appears under the correct IDS environment. If correct, this will then grant you access to the desired system and will log you in.
Extra Support
We have published an E-learning module that will guide you through the steps required to set up and use MFA:
If you require any further support please contact Liaison by email or call +44 (0)1242 388 531.
Frequently asked questions
If your question is not covered below please email [email protected]
No. HESA will not collect or store any new personal information as part of the authentication process.
The current planned date for roll-out of MFA is Thursday 21 April 2022. We will contact all users in advance to confirm this date or let you know of any changes to the schedule.
You will be asked to authenticate each time you log in to IDS.
No. You will only be able to authenticate via a third-party authenticator application, we do not currently support MFA via other methods such as SMS or Fido.
If your organisation provides a full-featured password manager as a desktop application or browser plug-in you may also be able to authenticate your IDS log-in by this means. See below for a list of authenticator apps and password managers which have been tested.
If your organisation’s MFA implementation has the ability to consume a QR code or manually enter a secret and provide a Time-based One Time Password then it is possible that you may be able use hardware tokens, however, we have not tested any hardware token solutions and so cannot provide any assurances to their suitability.
Some password manager applications can be used via a web browser plug-in. See the list below for some examples.
Our Time-based One Time Passwords are generated in line with industry standards, meaning that any mainstream authenticator app should be compatible, some password managers have also added support for this functionality too. Please contact your IT or Information Security department to discuss your requirements.
Examples of authenticator applications which we have tested prior to releasing MFA to the sector include those listed below. Please note that there are others available, and HESA does not endorse any particular third-party application for this purpose.
Examples:
Dedicated mobile Authenticator apps:
- Microsoft Authenticator
- Google Authenticator
- Keeper
- Duo Mobile
- LastPass Authenticator
Mobile password manager apps:
- 1Password
- Keeper Password Manager
- KeePass
Browser based password managers:
- 1Password
- Keeper Security
The Liaison team are available during usual office hours to support you. Email [email protected] or call +44 (0)1242 388 531.
Technical support for individual authenticator apps is provided by the app’s developers.
No. You must not use a shared account to access HESA systems. The IDS terms and conditions require that your credentials must be kept confidential and use of a shared log-in breaches this requirement.. Users must not attempt to use any third party software to allow the use of a shared email account.
Yes. If you also have an IDS account to access the Data Collection System, Graduate Outcomes or IMS you will need to install MFA separately for this account and your Beta account.
Are the IDS Terms and Conditions changing?
Yes. The Terms and Conditions for IDS have been updated to refer to the use of MFA. You will need to accept the updated T&Cs the next time you log in after the implementation of MFA.
Can you scan your QR code via your camera app?
No. You must scan your QR code via your authenticator app when adding a work account, and not scan the QR via your normal camera app.
